Openssl Pkcs11 Engine Slot
Openssl Pkcs11 Engine Slot Rating: 3,8/5 5567 votes
- Download openssl-pkcs11 packages for CentOS, Fedora. Fedora aarch64 Official openssl-pkcs11-0.4.10-5.fc32.aarch64.rpm: A PKCS#11 engine for use with OpenSSL.
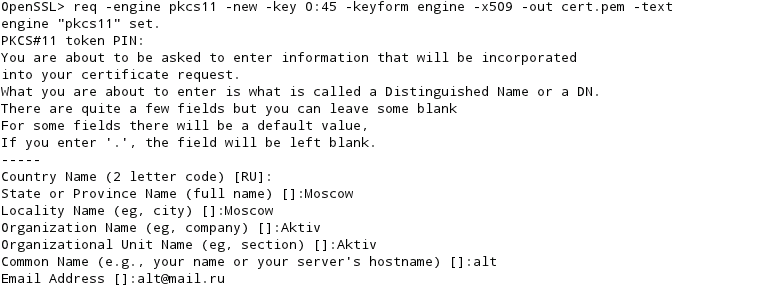
- Openssl rsautl -engine pkcs11 -keyform engine -inkey id6D796B6579 -sign-in datatosign.txt -out signature.dat KeyIdentification ”6D796B6579”isthehexvalueoftheString”mykey”(again,that’sthewayOpenSSL expectsit). Toverifythesignature,use: Console openssl rsautl -engine pkcs11 -keyform engine -inkey id6D796B6579 -verify-in signature.dat.
- Openssl rsautl -engine pkcs11 -keyform engine -inkey id6D796B6579 -sign-in datatosign.txt -out signature.dat KeyIdentification ”6D796B6579”isthehexvalueoftheString”mykey”(again,that’sthewayOpenSSL expectsit). Toverifythesignature,use: Console openssl rsautl -engine pkcs11 -keyform engine -inkey.
Openssl Pkcs11 Engine Slot Kit
> Hello,
>
> I want to write a program in which I can load a certificate from a smartcard instead of having it in a file on the client machine. In order to do so I will be using the opensc's engine_pkcs11 module. The module works fine using the shell but I want to implement it as an independent program. For example if I use the rsautl module then I can provide the inkey option and keyform option to use the private key from the smartcard. Look at the snippet below:
> openssl rsautl -sign -in file -keyform engine -engine pkcs11 -inkey slot_1-id_54a4c9bdaf3ff82b3367b586a6658c23 -out sig
> In order to do so I have to load the engine first. I do that as follows:
>
> openssl engine dynamic -pre SO_PATH:/usr/lib/engines/engine_pkcs11.so -pre ID:pkcs11 -pre LIST_ADD:1 -pre LOAD -pre MODULE_PATH:opensc-pkcs11.so
>
> which yields the result:
>
>
> (dynamic) Dynamic engine loading support
> [Success]: SO_PATH:/usr/lib/engines/engine_pkcs11.so
> [Success]: ID:pkcs11
> [Success]: LIST_ADD:1
> [Success]: LOAD
> [Success]: MODULE_PATH:opensc-pkcs11.so
> Loaded: (pkcs11) pkcs11 engine
>
>
> I want to do the same using C code in an independent program so that I can use the:
>
>
> static X509 *pkcs11_load_cert(ENGINE * e, const char *s_slot_cert_id)
> function to get the certificate from the smart card.
>
> So I tried to debug engine.c using ddd debugger to understand exactly which part of the code was required to just load the engine. In the same program I want to use the opensc function to load certificate directly from the smartcard and then use it in further server client communication.
>
Openssl Engine
Openssl Pkcs11 Engine
Sudo apt install libengine-pkcs11-openssl suisseid-pkcs11 opensc openssl osslsigncode swisssign-init. If you haven’t initialized your SuisseID, do it now. You should have received a TIN / PUK Sheet from SwissSign with the transport PIN (TIN). Run swisssign-init and follow the instructions. Set a PIN, that you will need below. Proof-of-concept of using an HSM to generate and store key pairs, then using those key pairs to create a CA certificate, client certificate and server certificate for TLS - arsing/openssl-pkcs11-demo.